Let your windows steal the show with fabulous new curtains and blinds. Whether you have a bay or straight window, discover the best way to dress it up?
Use a wave heading
Soft waves of fabric create a smart but simple finish that's easy on the eye. A wide Tempo heading pleat makes curtains fall in soft, regular waves, so they will always look just right. Team it with a sleek, modern suspension rail that the curtains glide below and let the curtains sit flush with the floor so they'll look neat open or closed.
Stylist's tips
A cut-velvet pattern adds a luxurious edge to this otherwise pared-down window treatment.
Where to buy
Curtains made in Bolivia 230 0321, £37 per metre, Camengo.
Use a double pole
Need to dress your window for privacy and prettiness? A double pole lets you do both
A clever double pole design means you can hang both a sheer and a curtain around the bay window, but draw them independently. Brackets normally get in the way of curtain rings being pulled around a bay, but this design uses passing rings that allow the curtains to be drawn all the way round. A standard heading tape left ungathered on both curtains creates a soft, informal effect. Keep the sheers sill-length for a neat finish and go for floor-length curtains to create real impact in a bay.
Stylist's tips
Team a bold, modern, floral curtain fabric with a floral patterned voile for a modern take on a curtain and sheer.
Where to buy
Curtains made in Samara J515F-01, £37 per metre, Jane Churchill. Voile curtains made in Sophia 074, £48 per metre, Harlequin. Fusion double curtain rail, custom-made by the Bradley Collection.
Use a pelmet
A neat, modern pelmet creates a smart, fuss-free finish in a large bay window
For a contemporary take on a traditional curtain finish, use a small pelmet that picks up one of the colours in the curtains. It gives a sophisticated finish to a bay window and means you can use a plain curtain track around the bay as it will be concealed by the pelmet. Team it with a curtain in a pinch pleat heading that creates regular gathers for an equally understated effect. A pair of holdbacks that match the pelmet is all that's needed when you want to draw the curtains back and let in maximum light.
Stylist's tips
For a hotel-chic window treatment like this, choose striped satin for a tailored look and give the pelmet a touch of decorative detail with a fringe trim.
Where to buy
Curtains made in Sapphira 8515, £48 per metre, Harlequin. Pelmet and holdbacks made in Jem silk in Maroon 33, £19.90 per metre, Linwood. Ruche trim JM38E-02, £27 per metre, Jane Churchill.
Use Four Single Curtains
Dress up your bay window with four sweeping curtains for an elegant finish
A pair of curtains hung centrally, plus a curtain to each side of the bay, makes an opulent alternative to a single pair of curtains. A flat-faced pole in a wood-effect and metal finish is a feature in itself - use a suspension-rail system so that the fabric gathers neatly below the pole and doesn't hide it. Position a holdback for each curtain two-thirds of the way up the window, so the curtains can be draped across the top part of the window when drawn open. Allow plenty of length on the curtains so they pool on the floor to complete the lavish look.
Stylist's tips
Repeating the colour of the curtain pole in the fabric's trim pulls the whole look together.
Where to buy
Curtains made in Sapphira 8515, £48 per metre, Harlequin. Pelmet and holdbacks made in Jem silk in Maroon 33, £19.90 per metre, Linwood. Ruche trim JM38E-02, £27 per metre, Jane Churchill.
Use Blinds and Curtains
Team blinds for controlling the light with dress curtains that frame the bay
Roll-up blinds are a fuss-free way to dress a bay. Go for a bold pattern that can be seen in all its detail and choose a complementary plain fabric for the back of the blinds so your window looks good from outside, too. Combine with an attractive pole around the bay and narrow dress curtains at either side. These provide a soft framing effect for the window, but can't be drawn closed. Snap-together rivets attach the curtain fabric to the pole for a neat, modern finish that doesn't require heading tape.
Stylist's tips Choose the same fabric for the dress curtains and the back of the blinds, as this will be on show when you roll them up during the day.
Where to buy
Curtains and blind backs made in Venice Grass, £27.75 per metre, Villa Nova. Blinds made in Osaka 658-26102, £14 per metre, John Lewis.
Use a Leading Edge
Create an eye-catching effect for a plain window with a vivid leading edge
A curtain with a leading edge is a real show stopper. A contrasting fabric from the back of the curtain is continued to the front, and simple holdbacks allow even more of it to be on show when the curtains are open. Use a simple pencil pleat and an unfussy pole to keep all the attention on the curtains themselves. You can enhance the effect of this stunning treatment by choosing a pole that's slightly wider than the window, which tricks the eye into thinking that the window is bigger than it really is and allows you to hold the curtains back without blocking light.
Stylist's tips
A satin-finish fabric for the leading edge gives it even more attention-grabbing shimmer.
Where to buy Curtains made in Stanza Onyx 1041/04, £20.50 per metre; Leading edge, backing and cushion made in Valetta Gerbera, £23.50 per metre; all Villa Nova.
Use Panels
Mix panels of plain and pictorial fabric for a window that's a real work of art
A fabric with a pretty illustration is a great way to dress up a window with an uninspiring view. Use plain fabric for two-thirds of the length, with the panelled pattern on the lower third. Create visual separation between the two with a ribbon braid, finishing off with a trim below. An eyelet heading on a pole means the fabric won't fold up, so the illustration can be seen clearly. Keep the curtains to sill height so they hang properly, draw easily and don't block heat from the radiator.
Stylist's tips
Choose a plain fabric in a paler contrasting colour and trim the join to make the print stand out.
Where to buy
Curtains made in Agean Blue, £8.99 per metre; Beaded trim, £5.99 per metre; both The Fabric Warehouse. Panels made in Petits Oiseaux in Framboise on White, £39.50 per metre, Brocante Fabrics.
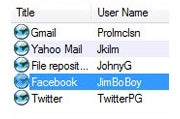
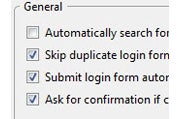 Little surprise that Secure Login provides a way to log you in to Web sites securely. It integrates with Firefox's password list--so when you visit a site, you can log in by clicking a button instead of having to type in your user name and password. Beyond that, Secure Login keeps your passwords safe in various ways. It stops any malicious JavaScript code from stealing your password, and it can block other password-stealing attacks, such as cross-site scripting (XSS) attacks.
Little surprise that Secure Login provides a way to log you in to Web sites securely. It integrates with Firefox's password list--so when you visit a site, you can log in by clicking a button instead of having to type in your user name and password. Beyond that, Secure Login keeps your passwords safe in various ways. It stops any malicious JavaScript code from stealing your password, and it can block other password-stealing attacks, such as cross-site scripting (XSS) attacks.